Secrets Management for the Secure Delegation of Authority
The Polykey platform helps individuals and organisations manage cybersecurity risks, by providing a platform for zero trust workflows. "SecretOps"



The Polykey platform helps individuals and organisations manage cybersecurity risks, by providing a platform for zero trust workflows. "SecretOps"




Eliminate Secrets Sprawl
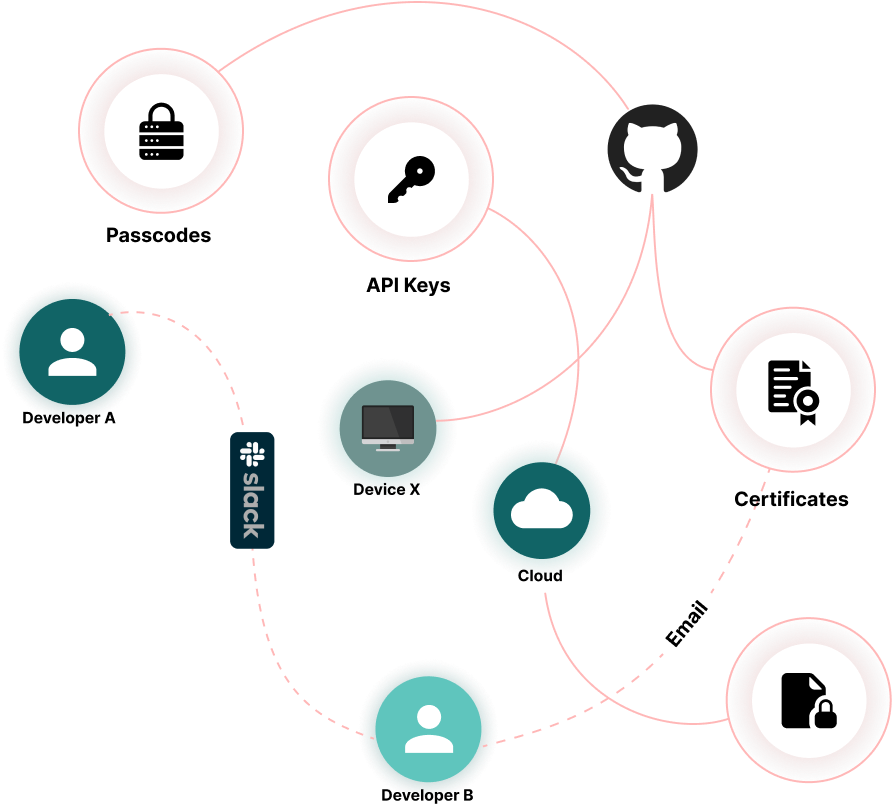

Exposed Environment Configuration
Use Polykey to keep secrets encrypted at rest. Temporarily inject when needed to bracket the authority
More Details Accidentally committing secrets to Git
Accidentally committing secrets to GitUse Polykey to keep secrets encrypted at rest. Temporarily inject when needed to bracket the authority
More Details Leaks through Insecure Channels
Leaks through Insecure ChannelsUse Polykey to keep secrets encrypted at rest. Temporarily inject when needed to bracket the authority
More Details Ambiguous and Opaque Tokens
Ambiguous and Opaque TokensUse Polykey to keep secrets encrypted at rest. Temporarily inject when needed to bracket the authority
More DetailsThe Core Principles of Polykey
Zero Trust of Delegation of Authority
Zero Trust of Delegation of Authority
Zero trust multi-party computation requires a system that understands secrets as tokenised authorities, and not just dumb strings.
Organisations have to delegate authority as they scale their digital and physical operations.
To this end, we are building delegation abstractions and logic built into Polykey as well as structured secrets for authority aggregation and attenuation.
Polykey can be integrated CI environments or other workflows, to enable zero-trust sharing of secrets and tracking of authority in the form of tokenised secrets.


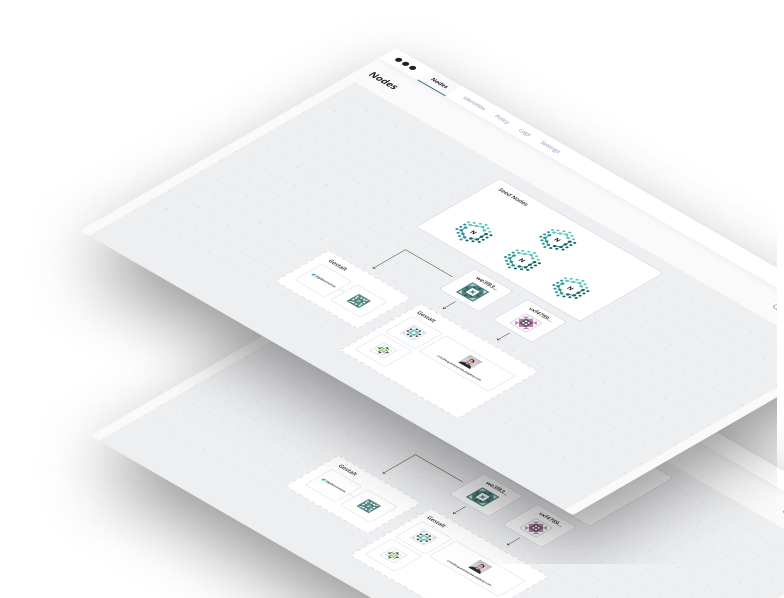
Local First Decentralized Encrypted Vaults
Local First Decentralized Encrypted Vaults
Fully private, no third party storage of your secrets. All secrets are stored in encrypted virtual filsystems known as Vaults. Vaults are version controlled with a real Git database. Vaults can be synchronized, backed up or shared (delegated) to your other Polykey nodes on other devices, or to other trusted parties.
Polykey is local-first or self-hosted by default. It is cloud optional. It automatically traverses network boundaries to enable seamless secure sharing.

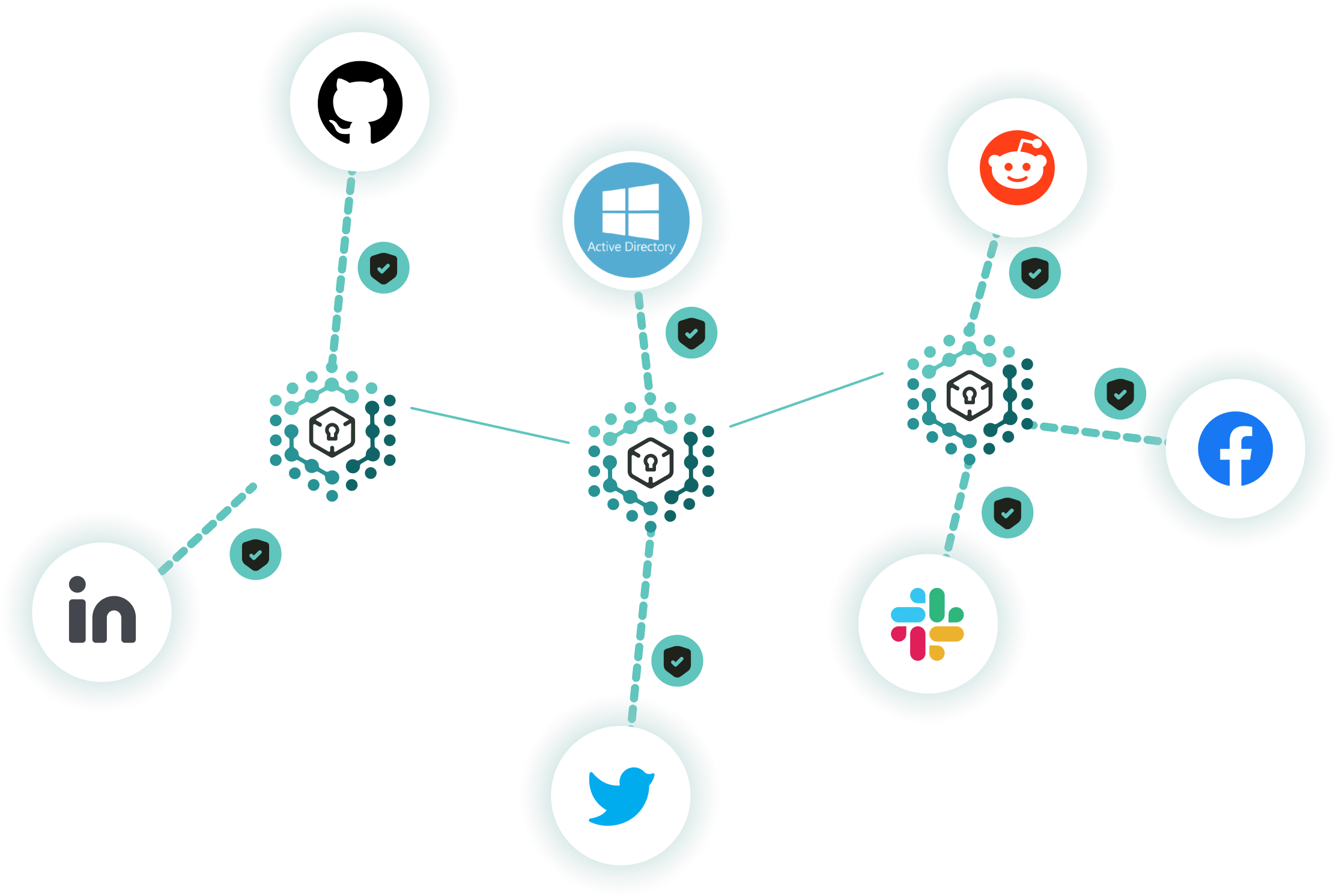
Discovery via Web of Social Trust
Discovery via Web of Social Trust
Claim digital identities by posting cryptographically signed messages. Discover trusted nodes by looking up well-known digital identities such as GitHub profiles.

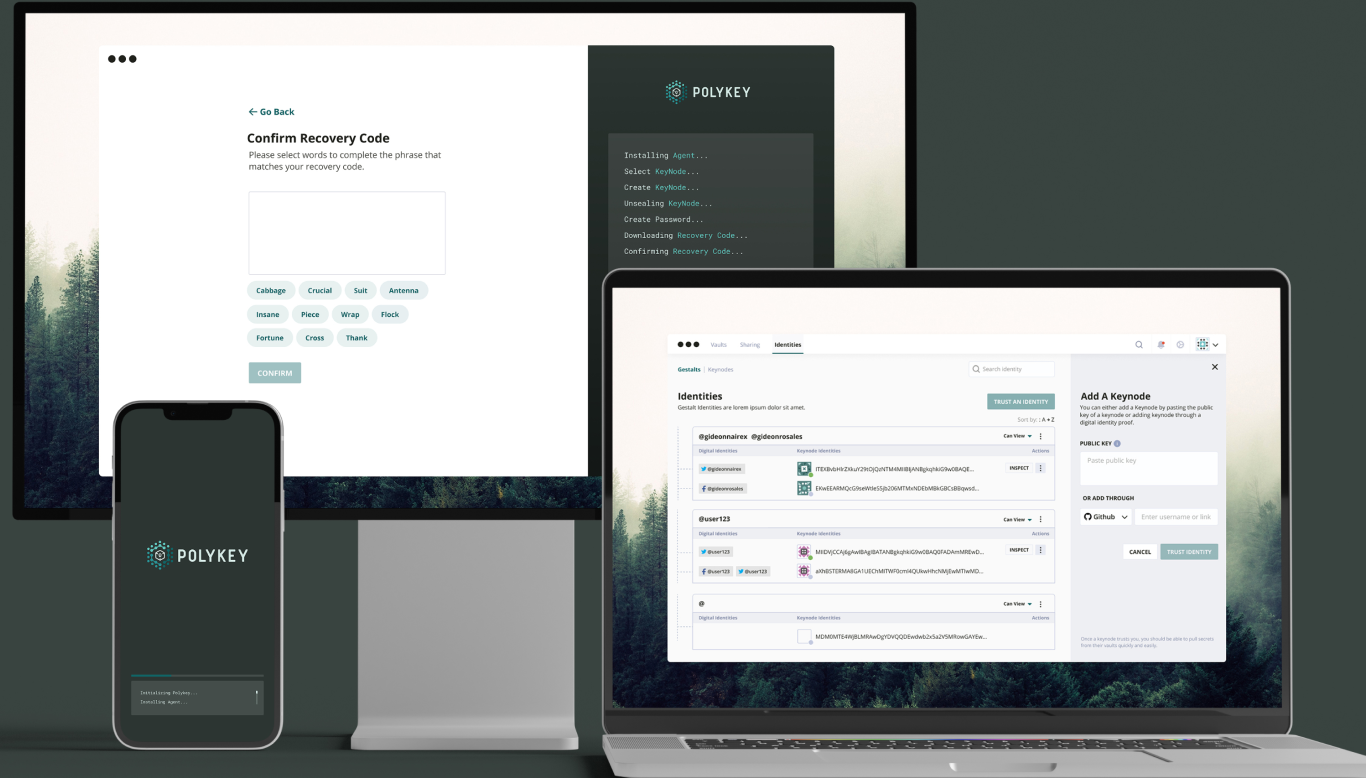
Polykey is an open source ecosystem. This includes the Polykey Core Library allowing programmatic integration. The Polykey Agent daemon that hosts a Polykey node.
The Polykey CLI client for developers. The Polykey Desktop and Polykey Mobile clients for the rest of the world. (Coming Soon)
Cross-Platform, Free, Open Source and welcoming of contributions.

COMING SOON
Polykey Enterprise Control Plane for Enterprise Private Networks
Use Polykey Enterprise to create a private network of Polykey nodes for your organisation.
- Visualize your cyber-physical infrastructure and its authority flows.
- Audit your authorisation flows and secret usage.
- Govern your authorisation with scalable policies.