Global/Public ACL and Trust Federation: Decentralized Authority Reimagined
Non-Fungible Tokens (NFTs) on the blockchain are more than just digital collectibles. They can act as decentralized form of internet capabilities/permissions to decentralized or centralized resources. This enables the creation of a global internet-wide ACL (Access Control List). Unlike centralized ACLs, where permissions are entirely controlled by the central platform, NFT capability ownership is maintained through decentralized consensus. This provides both censorship resistance and the ability to transfer permissions as assets. However, it has scalability drawbacks intrinsic to blockchain networks.
Centralized platforms can make use decentralized capabilities to gate features within their systems. For instance, Clarity.so has introduced token-based roles and permissions, allowing users to unlock features based on their possession of decentralized tokens. Similarly, platforms like Luma use NFTs to gate events, requiring attendees to hold specific tokens in their wallets for access. Below is an example of how Luma implements token gating for event registration:
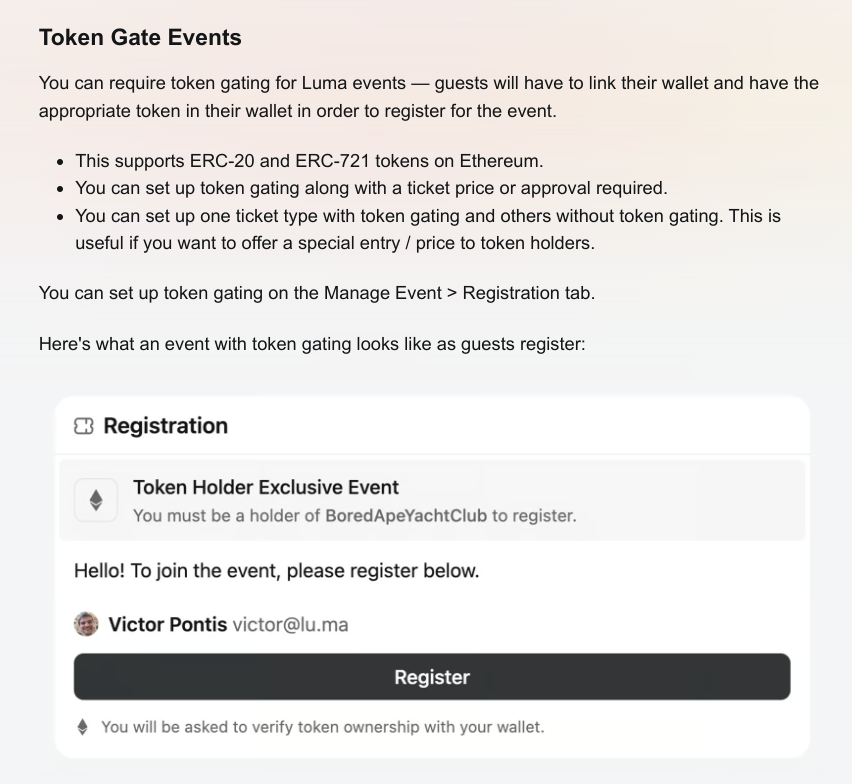
Why would centralized platforms open their security systems to the public blockchain? There could be benefits similar to why certain systems use "login via social network". The cost of implementation can be decreased, while leveraging pre-existing identity structures reduces the friction of onboarding for customers. Therefore at the same time, using NFT capabilities or fungible capabilities is way of leveraging a network effect of other public authority systems on the blockchain.
There are several problems with relying on NFTs as your permission system:
- Delegation of authority requires a transaction on the blockchain will cost some unit of energy.
- The authority structure is being revealed publically and this may not be suitable for privacy.
- The blockchain is being polluted with information that's only relevant to a subset of users.
- During high congestion, the cost to delegate will increase even more.
Before NFTs, tokenized capabilities existed in the form of JSON Web Tokens (JWTs). JWTs are self-contained bearer tokens, possessing the JWT as a string equals possessing the permission. This means the security of JWTs depend on the issuing system and the bearer system to securely manage the shared secret.
An example of JWTs in centralized systems are magic links. These magic links are a convenient way to grant temporary access to resources. However, using these links relies on out-of-band communication, potentially exposing the secret over insecure channels.
It is possible to avoid the problem of preventing exposure by changing the way ownership of the permission is expressed. Rather than simply bearing a secret token, the token can instead embed a claim that a particular identity has an authority. Then this is combined with a proof of authority that can be checked. The simplest proof is where the token is signed by a trusted authority, and the signature can be checked to be genuine. The user/program attempting access has to also prove that they are in fact the identity expressed within token claim. This can be achieved with the user/program's own signature.
Signed JWTs add a layer of asymmetric authority through a cryptographic signature from a trusted entity. This model doesn’t rely on decentralized consensus but rather on the trustworthiness of the signature’s authority. This makes it more flexible and scalable than NFTs but shifts security onto the reliability of the signing authority. What this means is that security of the signed JWT does not rely on secrecy. In Polykey, for example, signed JWTs could be made public to the network via the sigchain module.
In the signed JWT case, delegation of authority is not a simple matter of sharing a token. A derivative token must be minted that extends the authority to another identity.
A signed JWT doesn't have to be public, it can still be transferred secretly over secure channels, it just not catastrophic if it were exposed. However there could be benefits to public attestation to claims just like NFTs on a public blockchain.
Polykey enables the ability to manage both tokenized authorities such as JWT shared secrets and capabilities expressed through signed JWTs by creating a secure highway of authority. In scenarios where a more decentralized approach is needed, Polykey could integrate with Ethereum to mint NFTs representing access capabilities. These NFTs would be transferrable and verifiable through the blockchain enabling integration into further decentralized resources or centralized platforms relying on these public blockchain capabilities.
Polykey is also exploring the concept of federated tokens that operate across multiple domains or blockchains. These tokens could combine the best of both JWTs and NFTs, offering fine-grained control over permissions in a decentralized environment. Recent developments in Polykey, such as enabling nodes to access private networks through cross-chain interactions, underscore the potential for a federated trust model. By allowing nodes to issue and validate tokens across different networks, Polykey could create a scalable, flexible system for managing decentralized authority.
The issues Polykey#779 and Polykey#770 in our Polykey GitHub repository tracks our work on network segregation and authentication token logic. These developments are critical in ensuring secure and seamless access to private networks, enabling Polykey nodes to authenticate and operate within various isolated environments while maintaining decentralized integrity.
Enforcing policy across decentralized systems is challenging, especially when dealing with nodes not fully under central control. While decentralized networks offer resilience and flexibility, they also open the door to potential rule violations by nodes that may have been modified or corrupted. In Polykey, this challenge is addressed by leveraging its sigchain and decentralized architecture to ensure all nodes adhere to network policies. However, the need for full stack control becomes apparent when dealing with potentially rogue nodes that could hide unauthorized activities.
The convergence of NFTs, JWTs, and federated blockchains offers a tantalizing glimpse into the future of centralized and decentralized authority. By combining these technologies, we can create more resilient, scalable, and flexible systems for managing identities and permissions across multiple domains. As we explore these possibilities with Polykey, our goal is to create interoperable tokens that leverage both decentralized consensus and trusted authorities, paving the way for a new era of decentralized trust infrastructure.
Future discussions may focus on what it means to have a global ACL system where some kinds of access-control is mediated through the blockchain rather than ad-hoc trust networks between centralized platforms.