Architecting Anti-Fragile Trust at EthKL
Our global digital systems are dangerously brittle. It is a brittleness that can be felt first-hand crossing the new "digital borders" that define our lives. These systems are brittle by design, riddled with single points of failure, and utterly unprepared for the cascading shocks of a polycrisis world.
This post is based on a presentation that Matrix AI recently ran with EthKL on mid-2025.
If you prefer to watch a video on this content instead of reading:
Nine Circles of Digital Hell

It started with a mundane goal: charging an electric vehicle in Kuala Lumpur. The charger was cash-less and app-only. Simple enough. But the app was region-locked, invisible to my phone. So began a domino run through modern identity spaghetti.
Downloading the app required a burner Google account on local Wi-Fi with a
Malaysian IP. Registering required a local Malaysian phone number. Getting that
number required physically presenting the passport for KYC at a telco shop. With
the precious +60 SIM in hand, one could finally register, only to face the
final boss: a credit card the app would accept. A single failure at any point in
this nine-step Rube Goldberg machine, a rejected card, a bad IP, a corrupted
passport scan, would have left me stranded.
This isn't an isolated incident, just a different flavor of an old chaos. In the US, opening a bank account requires proof of address, which needs a lease, which needs a visa, which needs a travel record... It's an opaque web of interdependencies navigated by trial and error, a series of buggy side-quests masquerading as official process.
This brings us to a powerful realization, captured by Stafford Beer: "The purpose of a system is what it does." This friction isn't necessarily a grand conspiracy; it's the emergent outcome of institutional incentives that favor control over access. The system isn't broken, it's just not designed for you.
This leads us to a foundational error in how we conceptualize risk. We've been conditioned to think about it like an actuary, but we're facing problems that demand a systems engineer.
Actuarial, insurance-based thinking makes sense when risks are uncorrelated. An insurance company pools surplus capital to cover isolated house fires because it's statistically unlikely that every house will burn down at once. But what happens when the risk is systemic? What happens when a wildfire tears through the entire state, a flood submerges the whole city, or a bug in a core smart contract library is exploited? The model collapses.
In a systemic event, everyone's house burns down at the same time. The insurance company goes bankrupt. There is no surplus large enough to cover a system-wide failure. You cannot insure against this kind of risk; it must be engineered out of the system from first principles. Yes, re-insurance pools and state guarantees soften the blow, but even these schemes buckle when correlations hit 1.0. Therefore systemic risks require defense-in-depth and modular isolation that prevents cracks from propagating (exactly the principles upon which Polykey is built on), like the grain boundaries in a steel beam. It's a problem of materials science, civil engineering, and rational policy, not financial statistics.
Yet, this flawed, actuarial mindset has infected everything. We have begun to substitute spreadsheets for steel. We see the same tragic pattern in our healthcare system, which excels at financing intervention but fails at engineering prevention. Instead of engineering resilience, we buy insurance, trading structural integrity for a financial abstraction. It's a societal moral hazard that makes us feel safe while leaving us catastrophically vulnerable.
This is the Great Symbolic Drift. Our L1 systems, the abstract symbols of identity, credit, and risk have become dangerously untethered from the L0 material and engineering reality they are supposed to represent. We're living in a castle of abstractions built on foundations of sand, and the tide eventually comes.
The Panopticon, The Passkey, and The Security Theater
The castle of abstractions we critiqued isn't just an academic problem. It has real, sharp edges that define our relationship with power in both the public and private spheres. That flawed, actuarial mindset doesn't just produce brittle systems; it produces systems designed for control and liability-shifting, not resilience. Let's examine the two major fronts where this battle for your sovereignty is being waged.
The Human Front: When Your Phone Becomes a Leash
Do you own your identity? If you think having some crypto makes you sovereign, you are in for a ride. Identity is far more than money; it's who you are, who you represent, and your license to exist in the digital world. And right now, you don't own it.
The primary instrument of this dispossession is your mobile phone number. It has become the de facto global identity anchor, the "hot identity" more operationally significant than your passport. Each time a service demands your phone number, they shackle you to a state-controlled system. The passport scan for that SIM card, the video of your face for that new app, it's all part of a very bad deal.
The hidden logic is: "Our identity infrastructure is brittle, so we must take ownership of your device." Because they cannot trust you, they must trust the hardware they can co-opt, the secure enclave inside the phone you paid for. Control is silently slipping from users to a public-private mesh of regulators and platform owners. You don’t feel the hand on the leash until you try to pull away.
This is why even well-intentioned advances like Passkeys become a gilded cage. They offer a smoother user experience, but their recovery paths almost always lead back to the same centralized bigtech gatekeepers Apple and Google who act as deputies, verifying you against the very government documents and phone numbers anchored the old system. The state remains the identity of last resort, and the tech giants become its willing deputies.
This centralization loads a hair-trigger. A single, silent database toggle can freeze your economic pulse, severing your access to the digital world. History shows that such triggers, once built, are eventually pulled, often in a crisis where the definition of "good citizen" becomes conveniently narrow.
The complex web of dependencies also creates systemic sovereign vulnerabilities. The architecture is so fragile that a single exploit can ripple through entire populations. When this happens, the losses are socialized onto the users, and the crisis itself becomes the justification for even more centralized control. The cycle feeds itself.
The Machine Front: The Security Theater
This same flawed thinking in managing risk via abstraction and compliance rather than sound engineering manifests in the corporate world as "cybersecurity." The dominant model is a joke: build a perimeter, buy some "outside-in" security products, and then, most importantly, buy a cybersecurity insurance policy.
This is security theater: an expensive illusion that transfers blame faster than it patches code. The goal is not to engineer resilient systems, but to generate the paper trail necessary to satisfy auditors and insurance underwriters. Certifications like ISO 27001 and SOC 2 become legal artifacts for shifting liability, not technical guarantees of security. In this regime, large organizations don't engineer cybersecurity; they perform compliance.
This security-by-obscurity game is already failing catastrophically against human attackers. Now, consider the coming Cambrian explosion of non-human actors. The "secret sprawl" of API keys, tokens, and certificates for cloud services, IoT devices, and autonomous AI agents is growing exponentially. A compliance checklist cannot govern a fleet of collaborating AI agents. The outside-in, compliance-driven model will not just bend in this new reality; it will shatter. The systemic vulnerabilities being created right now are ticking time bombs.
A Builder's Manifesto: From First Principles to Anti-Fragile Trust
So, what can we do? This is not a lamentation; it is a call to create. It's a call to build technology that doesn't dispossess people, armed with a clear-eyed understanding of what all centralized entities ultimately want.
Before we can build, we must first define our terms. We must ask the most fundamental question, the one these brittle systems get so catastrophically wrong:
What is identity?
It is not a record in a database.
It is not an ID card.
It is not a symmetric or asymmetric key.
It is not a biometric template.
These are all just instruments. Brittle, static, forgeable instruments.
Your identity is a social relationship. It's a dynamic social process, not a static anchor. True, resilient identity is a social fact, a dynamic consensus among those who recognize you as a continuous process through time.
Once you understand this, everything changes. The absurdity of the current system becomes painfully clear. Why is bootstrapping an identity when you cross a border such a strange, friction-filled process? It's because the system is trying to map a static, instrumental credential (your passport) onto a dynamic, living reality. It will always be frustrating.
With this correct first principle in mind, the engineering requirements for a truly sovereign system become obvious. As a team, these are the principles that have guided our work. Let's use Polykey as an inspiration, as a case study in how to build from this foundation.
Principle 1: Verifiable Memory
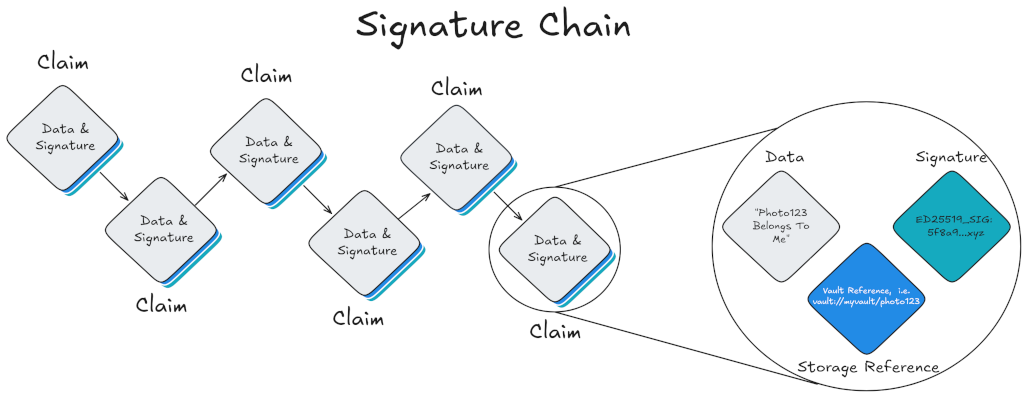
If identity is a social process that unfolds over time, then we need a way to reliably record its history. To build real trust, we must all have a stake in the observation of reality. A centralized database is not a shared memory; it is a liability, a tool for the powerful to rewrite history.
We need a new primitive. This is why Polykey is built on sigchains: per-node, user-owned, append-only ledgers of cryptographic claims. They are not just static logs, but composable, portable records of your digital relationships and delegated authority. They are designed to make security a first-class, programmatic concept from the ground up.
Principle 2: Pluralistic Sovereignty
If identity is a social consensus, then its recovery must also be social. The idea that you can be "deleted" because you lost a single instrument like a key, a phone, or a password, is an engineering failure born of a philosophical mistake. Resilience demands pluralism.
A sovereign system must therefore be recoverable through social consensus. This is why Polykey's architecture is built for social recovery, where a quorum of designated peers can collectively attest to restore a lost identity. Polykey's social graph called the Gestalt Graph recovers the individual node. (When all the Gestalt Graphs are put together, we create a Decentralized Trust Network) This is crucial because, as we'll see, even the strongest physical anchors can be lost. If we allow ourselves to be atomized into disconnected nodes, we become disposable cogs in a machine.
Principle 3: The L0 Anchor
To prevent the symbolic drift we’ve talked about, our digital systems need a provable, cryptographic link back to material reality. A social graph, no matter how resilient, needs a grounding in the physical world to prevent symbolic drift. Our answer to this "bits-to-atoms" problem is the concept of a Polykey Anchor.
This tethers L1 claims to L0 material facts. Building this at scale means working within the tightly-cartelized secure element ecosystem today, while paving the road toward verifiable, open hardware supply chains for tomorrow. True sovereignty requires it.
The Path Forward: An Asymmetric Strategy
Critique is not enough. We must build.
But we cannot fight the incumbent identity stack head-on; that's a battle of attrition we would lose. Our strategy must be asymmetric. We must find the cracks in the system, the points of leverage where a small force can produce an outsized effect.
For identity, the most potent maneuver is to Overlay and Invert.
You don't try to replace the existing rails overnight. Instead, you first build an overlay that is compatible with them. For initial onboarding, you accept the legacy credentials: the phone numbers, the emails, the passports. This minimizes friction and allows you to gain a foothold.
But here is the critical move, the point of leverage where the inversion happens. Your new layer must offer a more trustworthy, more portable, and fundamentally more resilient recovery mechanism.
Control of recovery is control of the root.
The legacy anchors are demonstrably broken. Email accounts get locked. Phone numbers are vulnerable to SIM swaps. Passports are useless for day-to-day digital recovery. When a user's new sovereign identity that is anchored by social consensus and a physical key becomes the most reliable way for them to recover their digital life, it becomes their true root of trust. Users and platforms will migrate to it, first for recovery, then for everything. At that point, the inversion is complete. The phone number and the passport are demoted to mere attributes attached to your new, sovereign anchor.
This is how we build systems that empower, not dispossess.
Thanks to EthKL for Hosting
This post is a crystallization of a presentation and, more importantly, a conversation I had the privilege of sharing with the EthKL community. The energy in the room was palpable, a clear sign that we are not alone in wrestling with these foundational problems.
The discussion that followed the talk was as illuminating as the presentation itself, quickly diving into the hard questions and exciting possibilities that arise from these ideas. I wanted to share a few of the key themes that emerged, as they point toward the collaborative work that lies ahead:
- The Abstraction Chasm: We had a great discussion tracing the line from
object-capabilities to serialized tokens like JWTs, and a shared realization
emerged: current tools create a "first-order box problem." When faced with
managing too many granular permissions, users and developers alike give up and
default to
grant ALL. This highlighted the deep need for a higher-order abstraction: a programmable, first-class concept of authority, touching on ideas from Datalog to modern knowledge representation, that can be composed and delegated safely. - Grounding The Digital in The Real: The L0/L1 distinction resonated deeply. The idea that "money" is just an entry in a database that can return "user not found" was a visceral moment. This led to a clarifying discussion about the Polykey Anchor, distinguishing its role as a hardware-based proof-of-action from a simple authentication tool like a Passkey. The Anchor's purpose is to tether the digital world to an undeniable physical event, and its irreplaceability is precisely what makes the social graph recovery mechanism a non-negotiable part of the architecture.
- Pragmatic Paths to Adoption: The conversation naturally turned to strategy. "How do we fight the incumbents head-on?" was revealed to be the wrong question. A more nuanced discussion about the Overlay and Invert strategy unfolded, focusing on pragmatic, asymmetric entrypoints. The consensus was that the most viable path is to first establish a beachhead in "greenfield" areas where legacy identity solutions are weak or non-existent, proving the model's resilience there before challenging the core human identity space.
- The Hardware Foundation: Finally, the discussion kept returning to a fundamental truth: software-only solutions do not grant full sovereignty. A system's claims can only be truly guaranteed if the hardware it runs on is verifiable. The group acknowledged that a long-term vision for anti-fragile trust must include a path toward verifiable, open hardware supply chains.
It's these kinds of conversations that transform ideas into movements. My deepest thanks to the organizers and attendees of EthKL for providing the forum.
If these questions and challenges excite you as much as they excite us, the conversation is only just beginning. Join us as developers, partners and pioneers building out this new Polykey substrate of trust.