Introducing Polykey - A Future Security Standard for Replacing Dotenv Libraries
As the landscape of software development evolves, securing sensitive data
remains a paramount concern. Traditionally, environment variables in
environments like Node.js, which extensively utilize .env files managed by
dotenv libraries, are prone to security risks. These .env files, while
straightforward, harbor significant security vulnerabilities. Sensitive
information such as API keys and database passwords are often stored in
plaintext, leading to potential data leaks if these files are not managed
correctly or accidentally committed to public repositories.
Polykey: Elevating Security and Efficiency
Polykey fundamentally transforms how environment variables and secrets are
managed, moving beyond traditional .env file approaches to a more secure and
robust system. Unlike .env methods that often expose sensitive data in
plaintext, Polykey entirely separates secret management from the codebase. This
separation ensures that sensitive information is never stored alongside code or
within project repositories, which dramatically reduces the risk of accidental
exposure.
Advanced Encryption and Secure Management
Polykey leverages the XChaCha20-Poly1305-IETF encryption algorithm, implemented through the Libsodium library, to secure secrets at rest and in transit. This modern cryptographic approach offers several benefits:
- Extended nonce size: Enhances security by enabling the safe reuse of encryption keys in various contexts without risking nonce collisions—crucial for dynamic and distributed applications.
- High performance: Designed for high-speed encryption and decryption processes, ensuring minimal impact on performance while maintaining robust security.
- Robust confidentiality and authentication: The algorithm guarantees that secrets remain confidential and verifiable, which is critical when handling sensitive operational data.
Enhanced Collaboration and Sharing
Polykey also facilitates secure end-to-end encrypted sharing of secrets, ideal for collaborative environments. When developers need to share environment variables or other configurations:
- Secure Sharing: Instead of sharing secrets over insecure channels or cumbersome setups, developers can share directly through Polykey’s encrypted vaults.
- Seamless Integration and Execution: Shared vaults can be directly integrated into another developer's local environment. Once a vault is copied to their node, they can immediately execute scripts or applications using the shared environment variables without further setup. This capability not only simplifies workflows but also ensures that all team members work with secure, up-to-date configurations without manual updates or risky data handling.
By eliminating reliance on .env files and integrating these advanced features,
Polykey significantly enhances the security posture of application deployments.
It addresses common security challenges associated with environment variable
management and sets a new standard for secure, efficient, and collaborative
development practices.
Applicability Across Programming Languages
Currently, Polykey's native support extends to JavaScript, TypeScript, and
Node.js environments, which commonly utilize .env files managed by respective
dotenv libraries. For other programming languages, interaction with Polykey is
facilitated through standard IPC, as direct RPC interactions are limited to
JS/TS/Node applications. For more details on library usage, refer to the npm
library @matrix/rpc.
Demonstration of Polykey's Capabilities
I created a GitHub repository to demonstrate the practical implementation and performance comparisons of replacing the traditional dotenv method with Polykey for a simple Node.js weather app. This showcases how Polykey can be effectively implemented in various environments where dotenv libraries are used. I encourage others to explore these demonstrations and consider similar implementations to witness the benefits firsthand. Follow the instructions in our README to perform the demo yourself, or view our detailed breakdown of the configurations and performance results of the dotenv-to-Polykey transition here.
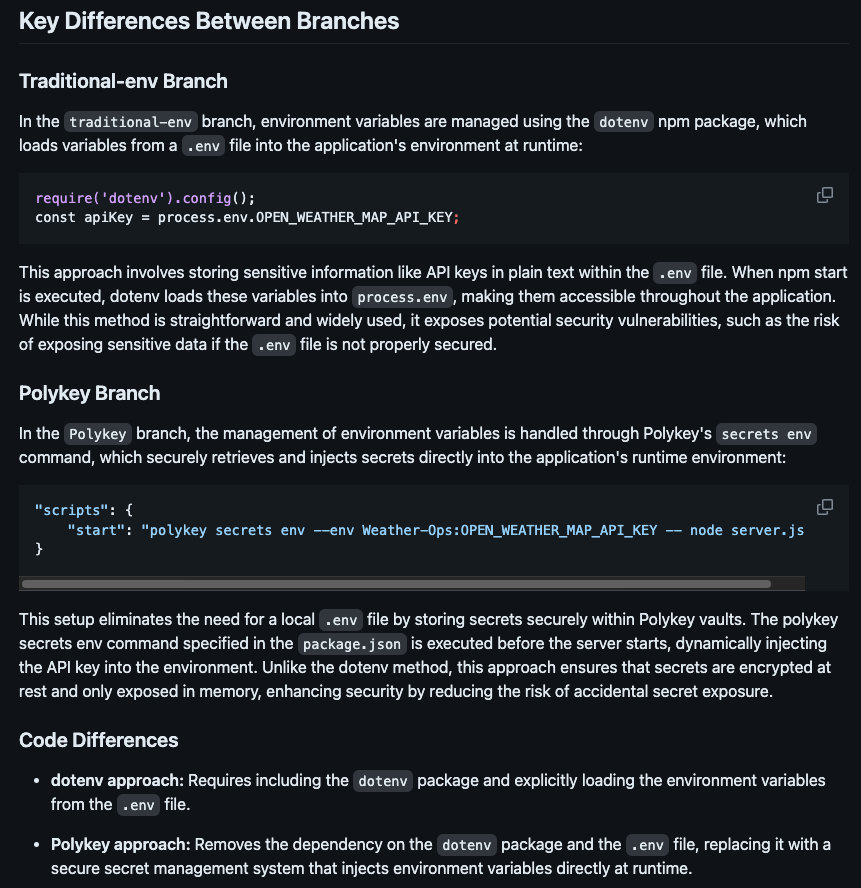
Future Directions and Call to Action
Currently, Polykey is optimized for development environments with plans to extend its functionality to production settings. This ongoing development promises to make Polykey a comprehensive solution for all stages of development, setting a new standard in the industry.
Conclusion: Join the Conversation and Shape the Future
We invite developers from all backgrounds to join this transformative journey by testing Polykey in your development environments and sharing your insights with us in our discord server. Your feedback is invaluable as we refine this tool into an industry standard. Stay informed on our developments for Polykey by following our open-source GH organization.
